Powerful tools for wallets, exchanges and trading platforms
Covesting is a software development company. We build cutting-edge solutions and partner with ambitious companies around the world.

B2B Software Inspired By Innovation
Covesting offers a comprehensive suite of investing and trading products that can be easily integrated into third-party apps. Covesting ecosystem currently consists of Copy-trading module, Yield accounts, Cryptocurrency exchange infrastructure, and finally the COV utility token that creates a user-centric economy on all supported platforms.

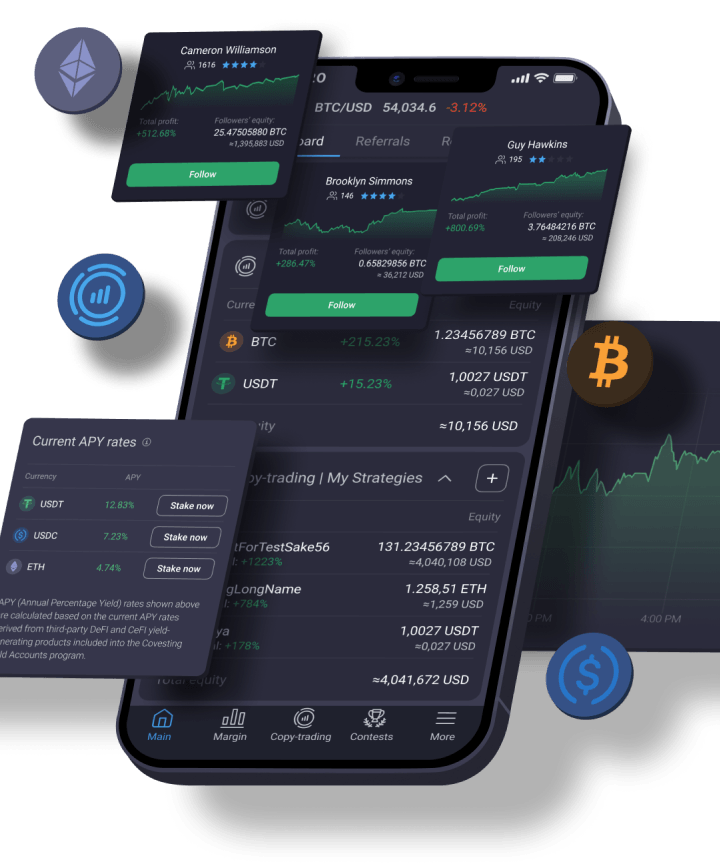
Covesting Copy-trading Module
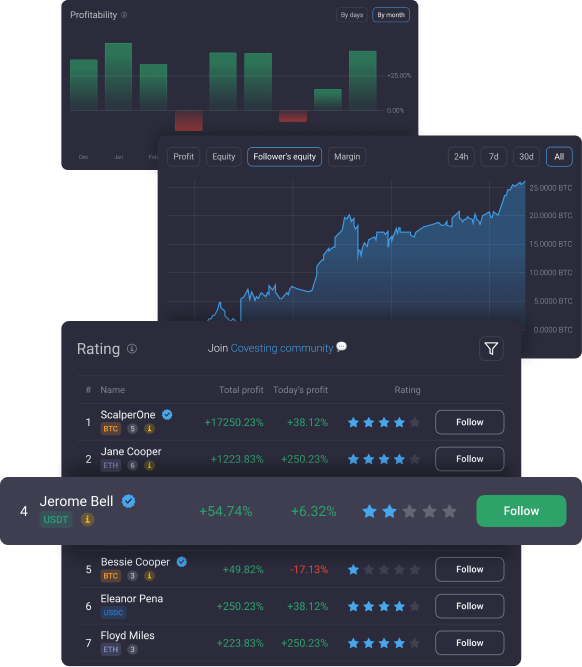
Copy-trading module is a flagship product of Covesting that allows you to track and automatically copy the trades of other users on the platform. Members can follow the best experts in the trading community, and benefit from their experience and winning strategies.
This tool is a perfect solution for exchanges and margin trading platforms that want to improve lead generation and boost their revenues. Contact sales
New to trading?
Choose among best performing strategies and automatically copy their trading activity to get the same returns!
Experienced trader?
Make additional income by allowing others to copy your trades! Get up to 20% of all profits earned for your followers.
(FX, CFD, Crypto)
strategies
return
Covesting and PrimeXBT to Launch Copy Trading in Groundbreaking New Partnership
The COV token, a utility token designed to unlock the potential of the Copy-trading Module, will be integrated into the PrimeXBT platform and become an essential part of the copy trading experience. Read more on Bloomberg
Building software for tomorrow
Flexible by design
All custom-developed B2B solutions can be white-labeled, licensed or fully owned by the institutional client

Bullet-proof
Our time-tested systems operate with 99%+ uptime and are highly reliable and scalable
Ever-improving
We release hundreds of improvements and upgrades each year to help our partners stay ahead of the industry
COV utility token
COV utility token is the backbone of the Covesting ecosystem, offering unique incentive schemes for a new generation of investors and traders. Whether it’s a trading discount or improved staking yield — Covesting (COV) token plays an integral role in all our applications.
COV activates one of three membership plans, depending on the amount of tokens staked. Based on the membership plan chosen - Advanced, Premium or Elite, users gain access to exclusive benefits and utilities within the Covesting ecosystem.

I have been impressed by the team’s drive and ambition to meet such a high standard in secure trading
The project features a comprehensive infrastructure and includes several big initiatives
Let’s Partner
Are you a trading platform, exchange, wallet, DeFI/CeFI app or a cryptocurrency startup? Contact our sales team to receive more information on how our solutions can help grow your business
Contact Us